SSRF URL Payload Encoding TryhackMe OWASP Top 10–2021 Task22 Explained
What is SSRF?
SSRF (Server-Side Request Forgery) is a security vulnerability that allows attackers to manipulate a server into making unintended requests to internal or external resources, potentially leading to unauthorized access, data leakage, or further exploitation.
TryHackMe Challenge Explained
The CTF challenge provides a URL http://10.10.182.198:8087/download?server=secure-file-storage.com:8087&id=75482342, which allows access to an Admin Area only from “localhost”. The goal is to manipulate the URL to access the Admin Area.
The solution involves changing the server parameter to http://localhost:8087/admin#&id=75482342. However, simply changing the server parameter breaks the link. To overcome this, the “#” character in the URL needs to be encoded as “%23”, resulting in http://localhost:8087/admin%23&id=75482342.
By inserting this modified URL into the original URL, you gain access to the Admin Area and retrieve the flag, demonstrating research and persistence in solving the challenge.
What is the technique here?
Encoding the “#” character as “%23” in the URL ensures that it is interpreted as part of the parameter value, not as a fragment identifier, preventing potential issues with how the server processes the URL.
Showcase by writing a Flask application
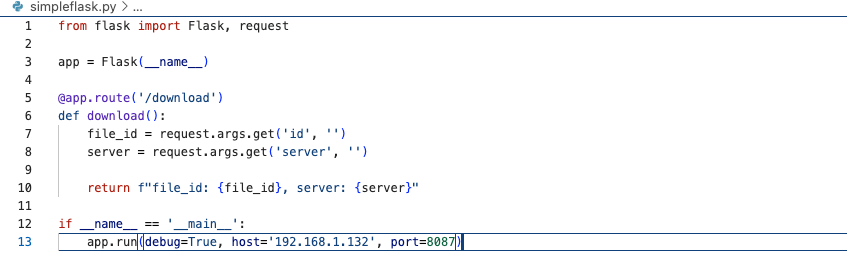
if we developing a basic Flask application and attempting to parse the server parameter, we encounter two distinct cases:
Case 1 encode “#” to “%23” (work)
In the scenario where we input http://192.168.1.132:8087/download?server=http://localhost:8087/admin%23&id=123, the server parameter resolves to http://localhost:8087/admin#.
Case 2 simply put “#” as it is (does not work)
However, if we input https://192.168.1.132:8087/download?server=http://localhost:8087/admin#&id=123, the server parameter is interpreted as http://localhost:8087/admin, omitting the # symbol after 'admin'. This discrepancy leads to the SSRF (Server-Side Request Forgery) request being directed towards unintended endpoints, thereby deviating from our original intended destination.
This distinction underscores the importance of handling URL parameters with precision, especially in scenarios involving sensitive operations like SSRF prevention.”
